How to Catch PDF Readers Red-Handed
🎯 The Ultimate Detection Mission
Want to know exactly who's reading your PDFs. when they're doing it. and what they're doing with the information? This comprehensive guide will teach you professional techniques to catch PDF readers in the act and gather irrefutable evidence of their activities.
⚠️ Legal Notice:
These detection techniques should be used only for legitimate purposes such as business intelligence, security auditing, or with proper authorization. Always comply with applicable privacy laws.
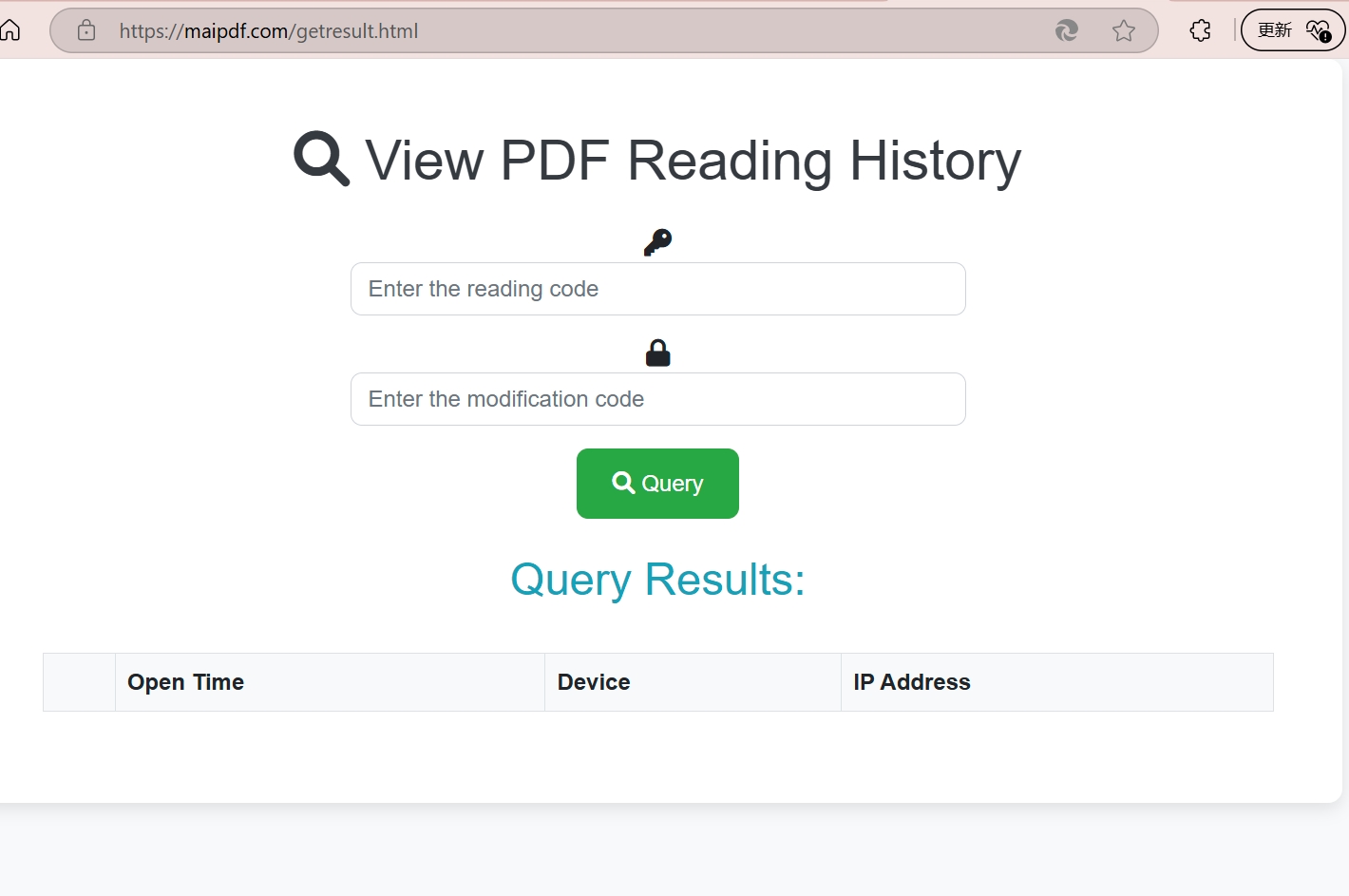
Flow Diagram
Interactive Flow Diagram
flowchart TD
A[Start] --> B[Process Step]
B --> C[Collect Data]
C --> D[Analyze Results]
D --> E[Done]
style A fill:#667eea,stroke:#764ba2,stroke-width:2px,color:#fff
style E fill:#48bb78,stroke:#38a169,stroke-width:2px,color:#fff
🕵️ Why You Need to Catch Readers
Critical Detection Scenarios
- Corporate Espionage Detection - Identify competitors accessing your confidential documents
- Leak Investigation - Trace the source of information breaches
- Client Engagement Analysis - Understand prospect interest levels
- Internal Security Auditing - Monitor employee access to sensitive materials
- Partnership Due Diligence - Verify partner engagement with shared documents
🔍 Professional Detection Methods
🎭 The Invisible Trap
Set up completely invisible tracking that catches readers without them knowing they've been detected.
Implementation Steps:
- Upload Target Document: Add your PDF to a professional tracking platform
- Configure Stealth Mode: Enable maximum invisibility settings
- Generate Trap Link: Create a link that appears completely normal
- Deploy Strategically: Share the link through suspected channels
- Monitor Silently: Watch for access attempts in real-time
🔗 The Honey Pot Link
Create irresistible "bait" documents that attract suspicious readers and capture their information.
Honey Pot Strategy:
- Compelling Content: Create documents that targets can't resist opening
- Strategic Placement: Position links where suspects are likely to find them
- Multiple Versions: Use different versions to identify specific leak sources
- Escalating Value: Make content seem increasingly valuable to encourage sharing
🧬 DNA Fingerprinting
Create unique document "DNA" for each potential reader to identify exactly who accessed what.
DNA Implementation:
- Unique Identifiers: Embed invisible codes specific to each recipient
- Watermark Variations: Subtle differences that identify individual copies
- Metadata Tracking: Hidden information that traces back to source
- Behavioral Signatures: Track unique reading patterns per user
📊 What You'll Catch Them Doing
🔍 Evidence You Can Collect
- Identity Information: IP addresses, geographic locations, device details
- Access Patterns: When they read, how often, and for how long
- Behavioral Analysis: Which sections they focus on most
- Sharing Activity: If and how they distribute your documents
- Network Analysis: Corporate vs. personal access patterns
- Device Fingerprints: Unique hardware and software signatures
🎯 Setting Up Your Detection Operation
🚨 Real-World Detection Success Stories
📈 Advanced Detection Analytics
🛡️ Counter-Detection Awareness
⚖️ Legal and Ethical Considerations
🚀 Next-Level Detection Techniques
